In the age of rapidly advancing technology, the vulnerability of encryption algorithms to quantum computing has become a major concern. Shor’s algorithm, utilized by quantum computers, poses a threat to asymmetric encryption methods such as RSA, DSA, ECDSA, and Diffie-Hellman, by efficiently factoring large numbers. This vulnerability could potentially compromise the security of sensitive data encrypted using these algorithms. Additionally, symmetric encryption algorithms like AES and SHA are also at risk due to Grover’s algorithm, which can find encryption keys much faster than classical computers. In this article, we will delve into the types of encryption algorithms that are vulnerable to quantum computing, the potential risks they pose, and the ongoing efforts to develop quantum-resistant algorithms.

Introduction to Encryption Algorithms and Quantum Computing
Explanation of encryption algorithms and their role in securing data
Encryption algorithms play a crucial role in securing data by converting plaintext information into ciphertext, making it unreadable to anyone without the proper decryption key. These algorithms have a long history, dating back to ancient times when methods like the Caesar cipher were used to protect sensitive information. In today’s digital age, encryption algorithms are essential for safeguarding data during transmission and storage, ensuring the privacy and integrity of personal and organizational information.
There are two main types of encryption algorithms: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption utilizes a pair of keys – a public key for encryption and a private key for decryption. These algorithms are widely used in various applications, including secure communication, online banking, e-commerce, and data protection.
Overview of the impact of quantum computing on encryption algorithms
Quantum computing has the potential to significantly impact encryption algorithms, particularly due to the threat posed by quantum computers to the security of current encryption methods. As quantum computers continue to advance, the risk of breaking traditional encryption techniques, such as RSA and symmetric encryption algorithms, becomes more pronounced. This is primarily attributed to the increased computational power of quantum computers, which can efficiently solve complex mathematical problems, including factoring large numbers, a task that poses a challenge for classical computers.
Specific vulnerabilities of encryption algorithms to quantum computing
One of the most notable vulnerabilities of current encryption methods to quantum computing is the susceptibility of asymmetric algorithms, such as RSA, to Shor’s algorithm. Shor’s algorithm has the capability to factor large numbers into their prime components at a much faster rate compared to classical algorithms, thereby compromising the security of data encrypted using RSA. Additionally, symmetric encryption algorithms are also at risk due to the potential efficiency of Grover’s algorithm, which can significantly reduce the time required to search for a specific key in a brute-force attack.
Efforts in developing post-quantum cryptography
In response to the potential threats posed by quantum computing, extensive research and development efforts are underway to create post-quantum cryptography that can withstand quantum attacks. Post-quantum cryptography includes various approaches, such as lattice-based cryptography, quantum key distribution, code-based cryptography, multivariate-based cryptography, and isogeny-based cryptography. These new cryptographic methods aim to provide secure alternatives that are resilient against both quantum and classical computers, ensuring the continued protection of sensitive information in the face of quantum advancements.
Role of NIST in standardizing quantum-resistant encryption algorithms
The National Institute of Standards and Technology (NIST) has taken a proactive role in standardizing quantum-resistant encryption algorithms, recognizing the need to prepare for a post-quantum world. NIST’s efforts involve soliciting and evaluating candidate algorithms for post-quantum cryptography, with the goal of establishing standardized cryptographic primitives that can effectively mitigate the vulnerabilities introduced by quantum computing. This initiative is essential for ensuring the widespread adoption of quantum-resistant encryption methods across diverse technological platforms.
Preparation for a post-quantum world
As the impact of quantum computing on encryption algorithms continues to unfold, it is imperative for data center managers, security teams, and stakeholders to prepare for the transition to a post-quantum era. This involves collaborating with experts in the field, staying informed about the latest developments in post-quantum cryptography, and planning necessary hardware and software upgrades to implement quantum-resistant encryption methods. By proactively addressing the challenges posed by quantum computing, organizations can fortify their digital security infrastructure and uphold the confidentiality of sensitive data in the future.
Vulnerability of Asymmetric Encryption Algorithms to Quantum Computing
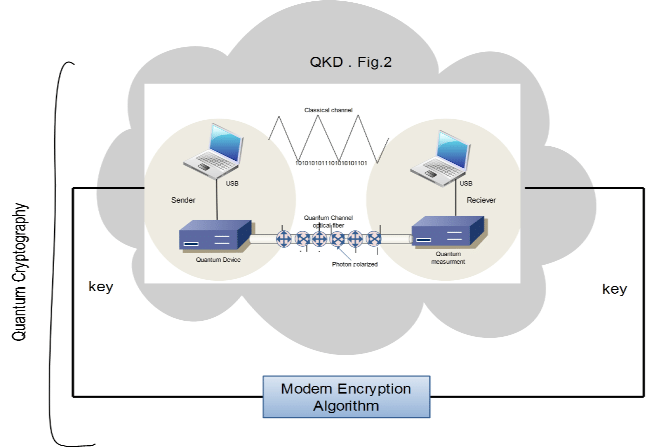
Explanation of asymmetric encryption methods such as RSA, DSA, ECDSA, and Diffie-Hellman
Asymmetric encryption, also known as public-key cryptography, involves the use of a pair of keys to encrypt and decrypt data. RSA, DSA, ECDSA, and Diffie-Hellman are common asymmetric encryption methods.
RSA: Developed by Rivest, Shamir, and Adleman, RSA is widely used for securing data transmission and digital signatures. It relies on the difficulty of factoring the product of two large prime numbers.
DSA: The Digital Signature Algorithm is a standard for digital signatures, ensuring the authenticity of digital messages or documents. It is based on the discrete logarithm problem.
ECDSA: Elliptic Curve Digital Signature Algorithm is a variant of the DSA, offering similar security with shorter key lengths, making it suitable for constrained environments such as mobile devices and smart cards.
Diffie-Hellman: This key exchange method allows two parties to establish a shared secret key over an insecure medium, enabling secure communication.
Discussion on how Shor’s algorithm poses a threat to asymmetric encryption

Shor’s algorithm, proposed by Peter Shor in 1994, is a quantum algorithm that can efficiently factor large numbers and solve the discrete logarithm problem. This poses a significant threat to asymmetric encryption methods, as it can compromise the security of RSA, DSA, and ECDSA.
The potential risks to data security due to vulnerability of asymmetric encryption to quantum computing
Quantum computing has the potential to render current asymmetric encryption methods obsolete, posing a significant risk to data security. The increased computing power of quantum computers could break the cryptographic strength of typical algorithms, highlighting the need for research in quantum-safe crypto algorithms.
The impact of quantum computing on asymmetric encryption methods
Quantum computing possesses unique computational capabilities that can render most asymmetric encryption algorithms vulnerable. This includes widely used algorithms such as DSA, RSA, and ECDSA, leading to the need for the development of immune asymmetrical algorithms such as Diffie-Hellman, AES, and SHA, which are resistant to quantum computing.
Risk to Symmetric Encryption Algorithms from Quantum Computing
Explanation of symmetric encryption algorithms like AES and SHA
Symmetric encryption algorithms like AES (Advanced Encryption Standard) and SHA (Secure Hash Algorithm) are widely used in securing sensitive data and communications. AES is a symmetric block cipher that uses a fixed key length of 128, 192, or 256 bits to encrypt and decrypt data. SHA, on the other hand, generates a fixed-size hash value from input data, making it suitable for verifying data integrity. These algorithms play a crucial role in ensuring the confidentiality and integrity of data in various applications, including secure email communication, web browsing, and data storage.
Discussion on how Grover’s algorithm can compromise symmetric encryption
Grover’s algorithm, a quantum algorithm developed by Lov Grover in 1996, has the potential to compromise symmetric encryption algorithms by significantly reducing the time required to search for encryption keys. While traditional computers would take years to break symmetric encryption, Grover’s algorithm running on a quantum computer could theoretically achieve this in a matter of days. This poses a serious risk to the security of data center assets, including storage and networking devices, as well as secure email and web browsing, as sensitive information could be exposed much more quickly than previously thought.
Impact of quantum computing on the security of symmetric encryption
The impact of quantum computing on the security of symmetric encryption is a major concern for organizations that rely on these encryption methods to protect their data. With the development of quantum computers, the security of symmetric encryption algorithms is at risk, and the potential for these algorithms to be compromised poses a significant threat to data confidentiality. As quantum computing becomes more widespread, the need for quantum-resistant encryption algorithms that can withstand attacks from quantum computers becomes increasingly urgent.
Development of Quantum-Resistant Encryption Algorithms
The development of quantum-resistant encryption algorithms is a crucial area of focus due to the looming threat posed by quantum computing to current encryption methods. Asymmetric encryption algorithms, such as RSA, are particularly vulnerable to quantum computing attacks, as they rely on the factorization of large prime numbers. To address this vulnerability, researchers are actively working to create quantum-safe cryptographic algorithms that can withstand such attacks. These new algorithms, although not yet proven or approved, are essential for ensuring the continued security of digital information in the face of advancing quantum computing capabilities.
Research and advancements in quantum-resistant algorithms
Research and advancements in quantum-resistant algorithms are vital for transitioning to encryption methods that can withstand quantum computing attacks. While symmetric algorithms like AES are currently considered safer than asymmetric ones like RSA, the landscape is likely to change as quantum-safe algorithms become more prevalent. As quantum algorithms improve, there is a possibility that certain encryption methods, such as hashing and substitution techniques, may become vulnerable. Therefore, the development of quantum-resistant encryption methods is critical for maintaining the security of digital data in the era of quantum computing.
Importance of transitioning to quantum-resistant encryption methods
The importance of transitioning to quantum-resistant encryption methods cannot be understated, especially as quantum computing continues to advance. While quantum computers have the potential to crack standard encryption methods, the development of quantum-resistant algorithms offers a solution to this threat. By focusing on encryption techniques that are secure against both quantum and classical computers, it is possible to prepare the current digital security infrastructure for the advent of quantum computers. This transition is essential for ensuring the long-term security and privacy of digital information in the face of evolving technological capabilities.
conclusion
In conclusion, it is evident that the advent of quantum computing poses a significant threat to the security of current encryption algorithms. Asymmetric encryption methods such as RSA, DSA, ECDSA, and Diffie-Hellman are vulnerable to quantum computing due to their reliance on mathematical problems that can be efficiently solved by quantum computers. Similarly, symmetric encryption algorithms like AES and SHA are at risk of being compromised by quantum computing, potentially exposing sensitive data to unauthorized access. The development of quantum-resistant encryption algorithms is crucial to mitigate the threat posed by quantum computing. Collaboration with experts in the field and staying informed about the latest developments in post-quantum cryptography are essential for organizations to prepare for the transition to quantum-resistant encryption methods. Additionally, planning necessary hardware and software upgrades to implement these quantum-resistant algorithms is imperative to ensure the security of data in the face of advancing quantum computing technology. As quantum computers continue to evolve, the need for robust and secure encryption methods becomes increasingly important. By understanding the vulnerabilities of current encryption algorithms to quantum computing and actively working towards the development and implementation of quantum-resistant encryption methods, organizations can safeguard their data and communications in the era of quantum computing.